Hello guys once again welcome, in this part, I will show how I solved other problems .let’s start
Challenge 3:
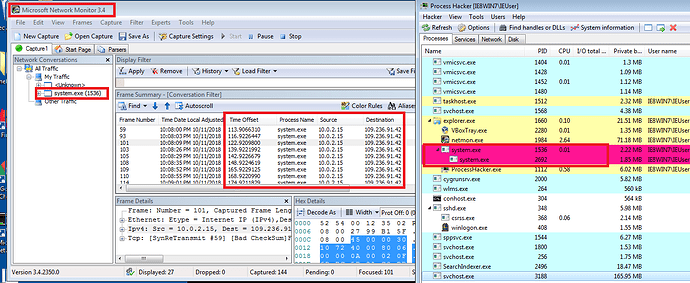
as description this is a malware analysis challenge on this challenge i have to find out C&C server (command and control server) you can learn more about command and control server just search on google ![]() .on this challenge I have to focus on when I execute this executable file what it does and I have to capture the requests that is made by this file. for find out the C&C server, I have to capture all request made by this file. I have used my virtual box (Windows 7) machine .when we do a malware analysis or reverse engineering we should use virtual box or VMware.I have used Microsoft network monitor for capturing requests. by this software, we can capture packets of a specific software .open up Microsoft network monitor start capturing mode and then just run that executable file.
.on this challenge I have to focus on when I execute this executable file what it does and I have to capture the requests that is made by this file. for find out the C&C server, I have to capture all request made by this file. I have used my virtual box (Windows 7) machine .when we do a malware analysis or reverse engineering we should use virtual box or VMware.I have used Microsoft network monitor for capturing requests. by this software, we can capture packets of a specific software .open up Microsoft network monitor start capturing mode and then just run that executable file.
also, i have open up my process hacker 2 for checking if this system.exe do any unusual things .so far we have got our C&C server.
Challenge 4:
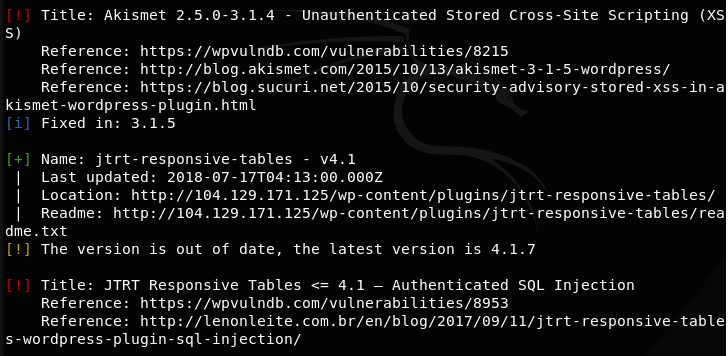
This is the interesting one web application exploitation .we just have to find out two vulnerability exist on this website .this was a Wordpress based website so I scan this site with wpscan for common vulnerability already discovered by security researcher and researchers.also i have run a custom dirscanner for any hidden directories and files.
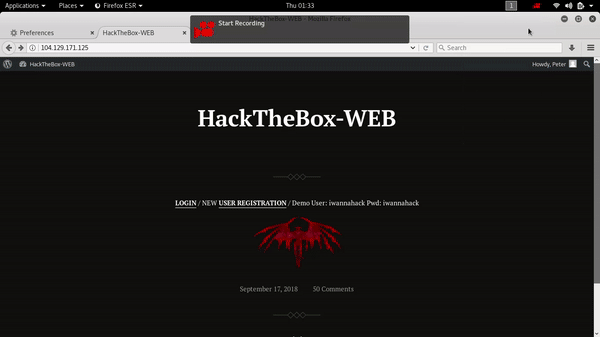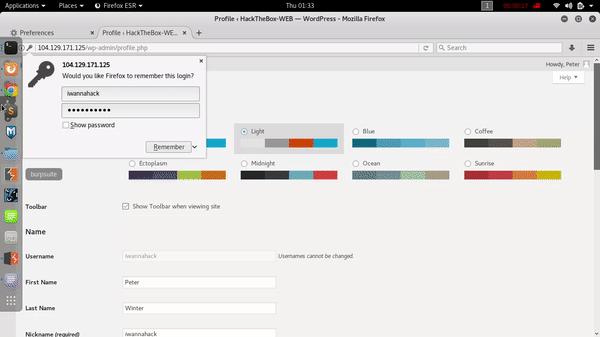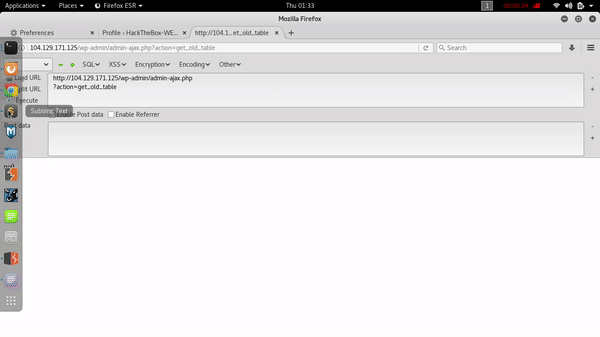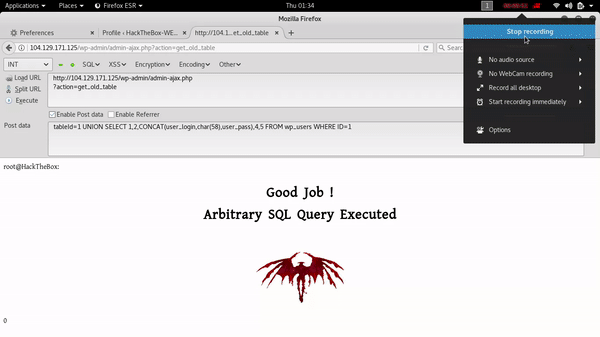
first of all i tried to exploit SQL injection vulnerability which was found by wpscan .you can find nice details and how can easily exploit this vulnerability here . my POC of SQL Injection :
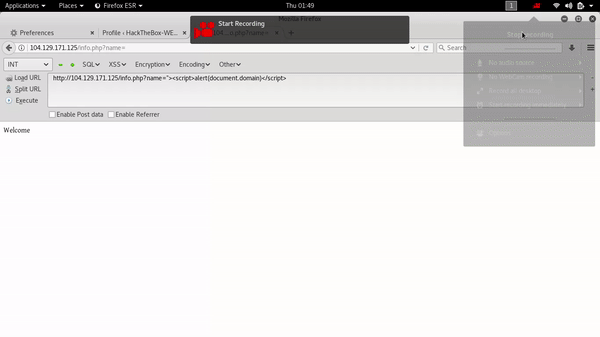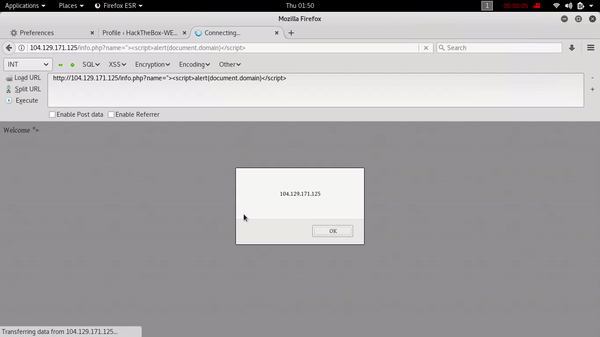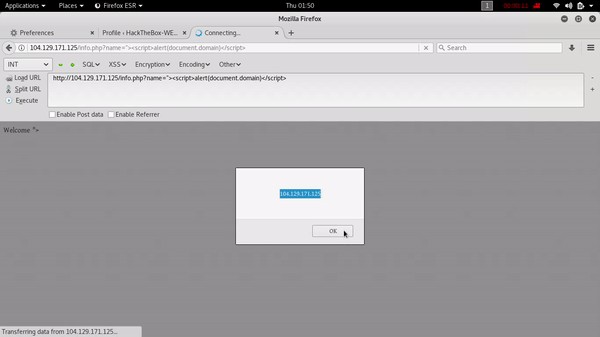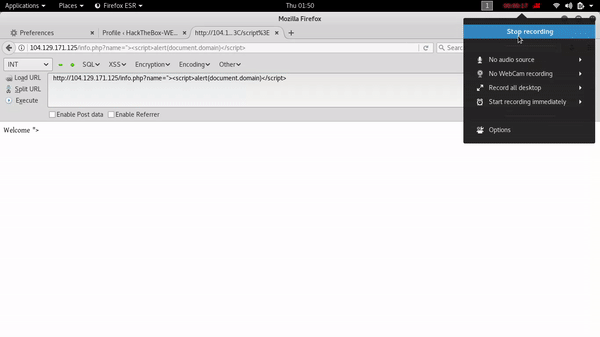
after finding this vulnerability i have started digging for another vulnerability dirscanner provide me some good result and one of them was /info.php and that was a little bit different than other results so i started digging on this one .finally i got xss on this one .my POC :
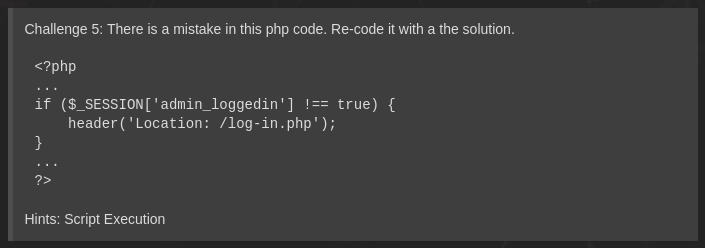
Challenge 5:
On this challenge, they provide us a PHP code and we have to fix this code, on this code there are two mistakes with that code. i have done a basic fix by just adding isset().
1 - Syntax Error
2 - Logical Error
In PHP in order to get get the value of session variable you use.
$_SESSION (It will get you the value of session stored)
1. if($_SESSION[‘admin_loggedin’] !== true); //it will not check the desired results for you, it will only check for the session at the database it is not checking the user anyhow.
If you want to check for the current browser which is accessing the admin panel you have to perform 3 checks:
1. isset()
2. !empty
3 $_SESSION == true // it is more preferred to store a session in some variable and then perform the comparison.
now the statement would become;
if ( !isset($_SESSION[‘admin_loggedin’] || empty($_SESSION[‘admin_loggedin’] || $_SESSION[‘admin_loggedin’] !== true )
{
header(‘Location: /log-in.php’) //redirection
}
BUT, even now this code is not secure because it will execute the lines after the of statement lets say our if statement is true and we have performed the redirection even then the below code will execute and admin would be bypassable.
so in order to make it more secure, you should use.
die();
this will not allow to execute the code below if statement.
i think i am clear now ![]()
rest of the code :
if ( !isset($_SESSION[‘admin_loggedin’] || empty($_SESSION[‘admin_loggedin’] || $_SESSION[‘admin_loggedin’] !== true )
{
header(‘Location: /log-in.php’) //redirection
die();
}
Thanks for reading .if there is any mistake sorry about that .please send me some feedback so that next time i can take care about my problems also if you guys have any question please let me know about it.
Thanks
@Khan